Cloudflare Tunnel for Secure HTTP Routing

Introduction
In today’s cloud-driven world, securely exposing internal services to the internet without worrying about network configuration complexities is crucial. Cloudflare Tunnel provides a secure way to route HTTP traffic from your origin servers to the internet without opening ports or configuring firewalls manually. This article explores how Cloudflare Tunnel works and how you can set it up for secure HTTP routing.
What is Cloudflare Tunnel?
Cloudflare Tunnel, previously known as Argo Tunnel, acts as a secure gateway between your server and Cloudflare’s network. It allows you to expose web applications without making your origin server publicly accessible. Instead of exposing your infrastructure to the internet, Cloudflare Tunnel securely routes requests through Cloudflare’s global network, ensuring protection against DDoS attacks and unauthorized access.
Benefits of Cloudflare Tunnel:
No Open Ports: Eliminates the need for exposing ports to the internet.
Automatic HTTPS: Cloudflare provides SSL encryption by default.
DDoS Protection: Cloudflare’s security stack protects against attacks.
Access Control: Integrates with Cloudflare Access for authentication.
Reduces Latency: Routes traffic through Cloudflare’s global network for faster access.
Setting Up Cloudflare Tunnel for HTTP Routing
Follow these steps to set up Cloudflare Tunnel and securely route HTTP traffic to your internal services.
Login to Cloudflare zero trust dashboard Cloudflare One
Navigate to Networks > Tunnels
Click on Create a tunnel
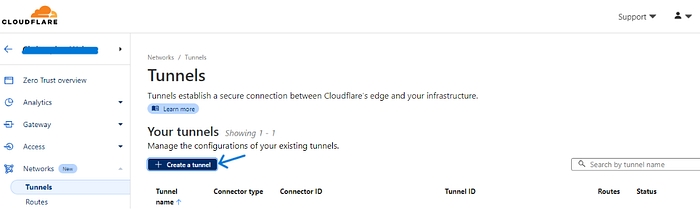
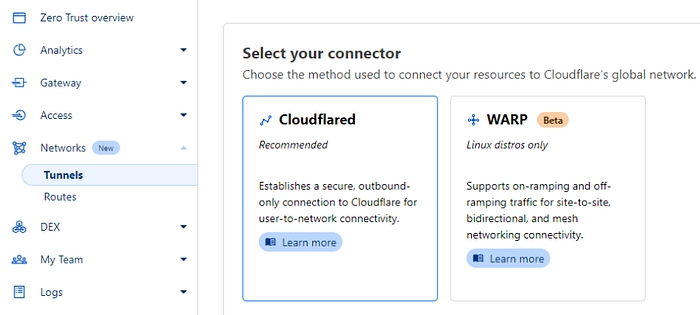
Select Cloudflared connector
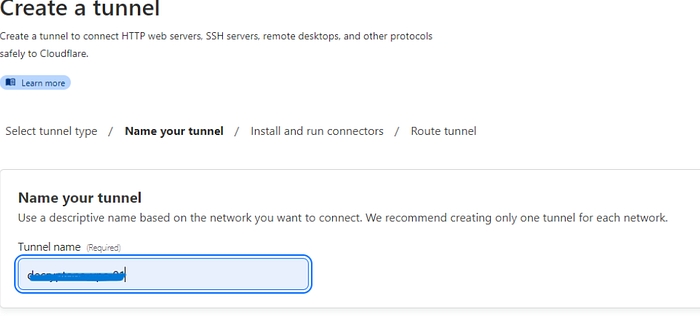
Name your tunnel
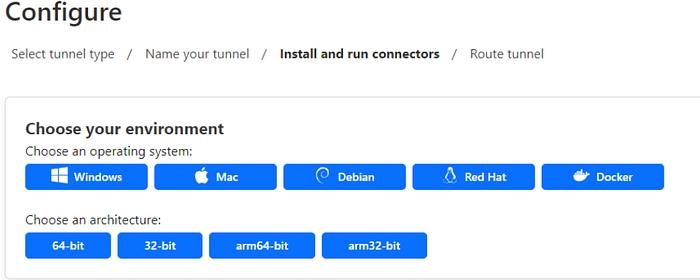
Install and run connectors
Choose an Operating system
Choose Architecture
Login to the server where you want to install the tunnel
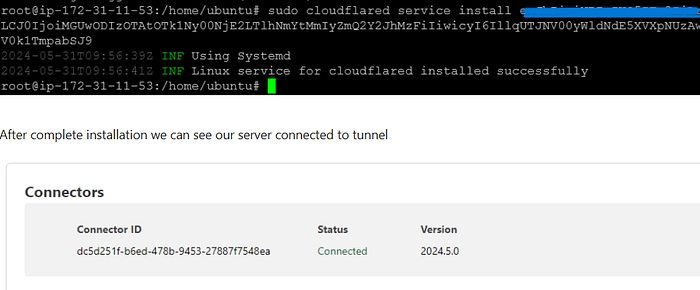
Run a command given by Cloudflare
After complete installation, we can see our server connected to the tunnel
Add networks CIDR block (AWS VPC’s CIDR) (Optional)
Add Domain to route and local Service
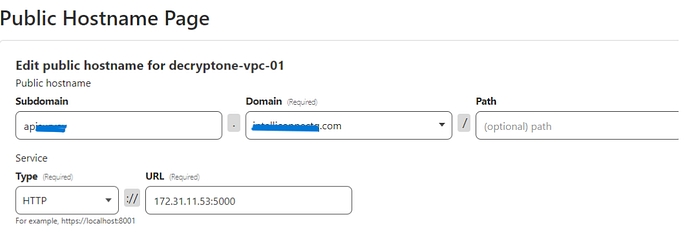
Now, check whether the domain is routed to the service or not.
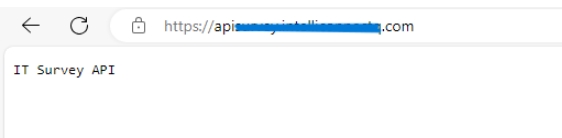
Great! We are done!
Conclusion
Cloudflare Tunnel simplifies HTTP routing by securely exposing services without compromising security. With features like automatic HTTPS, DDoS protection, and access control, it’s a powerful solution for securing web applications. By following these steps, you can set up Cloudflare Tunnel and ensure a safe and efficient deployment of your web services.
Last updated