Top DevOps/SRE Interview Questions and Answers on AWS VPC

What is AWS VPC (Virtual Private Cloud)?
AWS VPC: A Virtual Private Cloud (VPC) is a logically isolated section of AWS that you can use to launch AWS resources in a virtual network. It gives full control over network configuration, including IP address ranges, subnets, route tables, and network gateways.
2. How does VPC peering work, and what are the primary use cases and limitations for using VPC peering connections in Amazon VPC?
VPC peering is a networking connection between two Amazon VPCs, enabling private communication across AWS accounts or regions. It establishes a direct network route using private IP addresses, maintaining security and isolation.
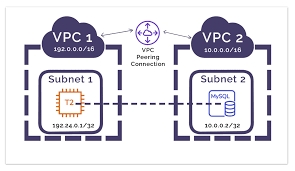
Primary use cases include: 1. Resource sharing: Access resources like databases or applications in another VPC. 2. Consolidated management: Centralize monitoring/logging services for multiple VPCs. 3. Workload separation: Isolate different environments (e.g., development, production) while allowing secure communication.
Limitations include: 1. No transitive peering: Direct connections only; must create separate peering for indirect communication. 2. Overlapping CIDR blocks: Not allowed; reconfigure IP ranges if necessary. 3. Edge-to-edge routing: Unsupported for VPN connections or AWS Direct Connect. 4. Cross-region latency: Higher latency when peering across regions compared to within the same region.
3. Explain the differences between security groups and network ACLs in Amazon VPC, and provide examples of when you would use each in your architecture.
Security groups and network ACLs are both essential components of Amazon VPC for securing resources. Security groups act as a virtual firewall at the instance level, while network ACLs function at the subnet level.
Security groups are stateful, meaning they automatically allow return traffic for permitted inbound requests without needing explicit rules. Network ACLs, on the other hand, are stateless, requiring separate rules for inbound and outbound traffic. Additionally, security groups support only “allow” rules, whereas network ACLs can have both “allow” and “deny” rules.
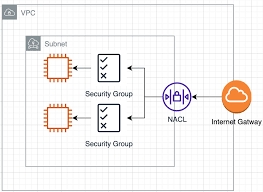
In your architecture, use security groups to control access to individual instances or groups of instances with similar requirements. For example, you might create a security group allowing SSH access from specific IP addresses for administration purposes.
Network ACLs should be used to provide an additional layer of security by controlling traffic flow between subnets. For instance, you could configure a network ACL to deny all traffic from a public-facing subnet to a private database subnet, ensuring data remains secure.
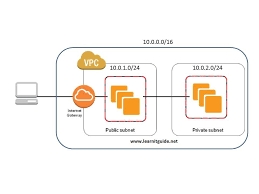
4. How would you design a multi-tier application architecture in Amazon VPC that securely separates public-facing components from private components?
To design a multi-tier application architecture in Amazon VPC, follow these steps:
Create a VPC with multiple subnets: public and private. 2. Deploy public-facing components (e.g., web servers) in the public subnet, ensuring they have Elastic IP addresses for internet access. 3. Place private components (e.g., databases) in the private subnet, without direct internet access. 4. Use security groups to restrict traffic between subnets; allow only necessary ports and protocols. 5. Implement Network Access Control Lists (NACLs) as an additional layer of security, controlling inbound and outbound traffic at the subnet level. 6. Utilize AWS services like Application Load Balancer (ALB) or Elastic Load Balancing (ELB) to distribute incoming traffic across instances in the public subnet. 7. Employ NAT Gateway or NAT instance in the public subnet to enable private instances to access the internet for updates and patches while preventing inbound connections.
5. What are the limitations of NAT gateways in Amazon VPC, and how can you mitigate potential bottlenecks caused by this limitation?
NAT gateways in Amazon VPC have limitations, including bandwidth constraints, single availability zone dependency, and limited IP port range. To mitigate potential bottlenecks:
Scale horizontally by creating multiple NAT gateways across different subnets and distributing traffic among them. 2. Use Elastic IPs to increase the available IP port range for outbound connections. 3. Implement a third-party NAT solution or configure your own NAT instance for more control over performance tuning. 4. Monitor CloudWatch metrics to identify performance issues and adjust resources accordingly.
6. What is the Difference Between VPC Endpoints and NAT Gateways?
VPC Endpoints
VPC Endpoints provide private connectivity between your Virtual Private Cloud (VPC) and supported AWS services without requiring an Internet Gateway, NAT device, VPN connection, or AWS Direct Connect. This keeps traffic within the AWS network, enhancing security and potentially reducing costs. VPC Endpoints are particularly useful for accessing services like S3 and DynamoDB securely and cost-effectively, as they often incur lower data transfer costs compared to other methods. They are ideal for applications that need secure, private communication with AWS services.
NAT Gateways
NAT Gateways enable instances in a private subnet to connect to the internet or other AWS services while preventing inbound internet connections. They are essential for scenarios where instances need to access external resources, such as software updates or third-party APIs. However, NAT Gateways can be more expensive due to hourly charges and data transfer costs, making them less cost-effective than VPC Endpoints for certain use cases. They simplify management by acting as a single resource per availability zone but may lead to higher costs as usage scales.
7. What is NAT Gateway?
A NAT Gateway (Network Address Translation Gateway) is a managed AWS service that enables instances in a private subnet to securely access the internet or other AWS services while preventing unsolicited inbound traffic from reaching those instances. It operates by translating the private IP addresses of the outbound traffic to a public IP address, allowing responses to be routed back to the originating instance. NAT Gateways must be deployed in a public subnet and require an Elastic IP address for internet connectivity. They are designed for high availability and can automatically scale to accommodate varying traffic loads

Amazon VPC is the backbone of AWS networking, providing secure and customizable virtual networks for your applications. Understanding core VPC concepts such as subnets, route tables, security groups, and gateways allows you to design flexible and scalable architectures.
Thank you for reading!🙏 If you enjoyed this article and want to stay updated with more content like this, follow me on my social media channels:
YouTube: Techwithpatil
LinkedIn: Tech with Patil
Instagram: techwithpatil
Feel free to connect, and let’s continue the conversation!😊
🚀 Struggling with Kubernetes Concepts? We’ve Got You Covered!
This course simplifies everything with: ✅ Real-world examples to connect theory with practice. 🛠️ Hands-on labs to build confidence through action. 📚 Clear explanations that make even complex topics easy to understand.
👉 You won’t find a better way to master Kubernetes! Enroll Now https://cloudops0.gumroad.com/l/k8s and take the first step toward becoming a Kubernetes pro! 🌟
AWSNetworkingCloud ComputingNetworkVpc
![]() Written by techwithpatil150 Followers·260 Following
Written by techwithpatil150 Followers·260 Following
DevOps | SRE | Carrers | Cloud | AI | Software Automation https://techwithpatil.com
Last updated